As we all know, Cryptocurrencies are founded and secured by a mathematical process called computational Cryptography; Thanks to this, information can be stored in the safest way without worrying that someone can make any changes or distort said information.
When we talk about the hash function within a computational process, we refer to the name of the Cryptographic function that is used for some computer process, which is of vital importance and very relevant in security and information protection processes.
These Cryptographic functions have a basic objective in all computer systems, this objective is to be able to encode the data of a system allowing the creation of a unique sequence of characters regardless of the amount of information that is being entered or encrypted.
Thanks to these Cryptographic functions, today we can safeguard and ensure the veracity and authenticity of the data, we can also safely enter passwords and sign documents in digital rooms.
Cryptography and Hash functions are widely used within the security system of Blockchain platforms and networks; The first Cryptocurrency to use this Hash encryption methodology was Bitcoin, which was developed by Satoshi Nakamoto.
The work carried out by the different hash functions is practically the same in any Blockchain, since they help to protect the data and prevent its reproduction. But not all these functions are the same and there is no exclusive function to protect Blockchains through encryption, since there are different types of hash algorithms that can be used depending on the case and the design of the Blockchain.
We can find various encryption standards throughout history, but the most significant are MD5, RIPEMD, and the SHA standard. Each one was very safe in its time of use and some are more secure and complex than others as we will see below.
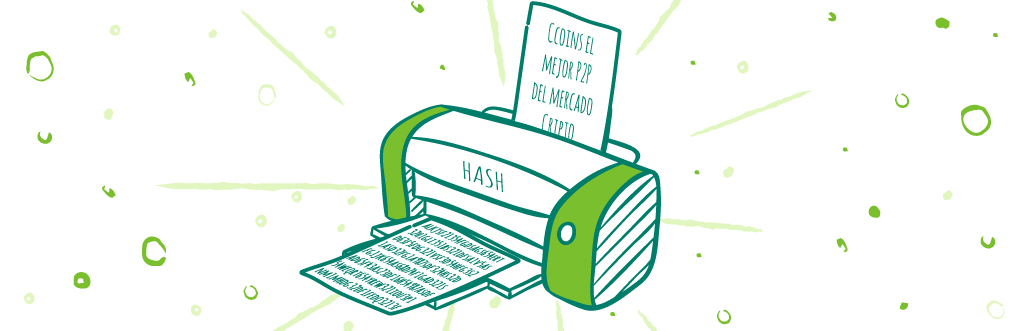
Hash functions operate thanks to a complex system of mathematical and logical processes that are responsible for converting base information into a unique code that represents said information. Sometimes these mathematical processes are implemented or executed within a software or program to be used within a computer system.
The basic idea of encryption by means of Hashes is that thanks to these programs any series of data or information can be taken and encryption processes applied, where the previously entered data will be subjected to the algorithms within the computer program, once completed the process we will obtain a string of characters with a fixed length, this length depends on the Hash function that is applied in the process.
Thanks to this conversion process to which the data is subjected, it makes said result in Hash practically impossible to convert again. That is to say, it is virtually impossible to convert a Hash code into the original data, since these systems were designed to be used in only one direction.
An example of how the conversion process works through SHA-256 when encrypting information:
Normal: Ccoins The best P2P in the Crypto market
SHA-256: 763a0794524f886734b0d71424c474108361234991c6c184b0072f4d5a7ced45
Although it is almost the same text, except that one letter is omitted at the end, we can see that the Hash code in SHA-256 changes.
Normal: Ccoins The best P2P in the Crypt market
SHA-256: 7e4b1e441464fd7f8fd500c7db5e398d76022fb90c3c993f0a9d7ef99d41d331
The process of conversion or encryption of information in Cryptocurrencies is carried out within the Blockchain network thanks to the computational power of the miners, in a Cryptocurrency the information that is used within said process is all the information referring to the transactional data that is stored in a block, such as the number of coins being sent, the date, the address of the person receiving, the address of the person sending, among other technical data.
Only in Ccoins, Buy and Sell your Cryptocurrencies at the best price through hundreds of offers in our P2P market or convert them to any of our 30 available cryptocurrencies.
Ccoins is the fastest and safest platform to trade crypto assets
Not in the slightest, hash technology is used in countless computer security and communication processes globally, it is true that these processes became popular thanks to Cryptocurrencies such as Bitcoin, but this technology was not used for the first time in Cryptocurrencies anymore. that its first use was to authenticate electronic documents.
This is due to the fact that this technology is the most powerful encryption hash function currently known, and also due to its one-way characteristic, it does not allow a Hash to be converted back into the original information, giving anonymity and maximum information security.
No, it is true that many Cryptocurrencies make use of the SHA-256 Hash function but this is because many of them are copies or use the Bitcoin code as a base, but there are many other popular Cryptocurrencies that make use of other encryption algorithms.

Download the app for your mobile device here:
Register your email and get early access and benefits.